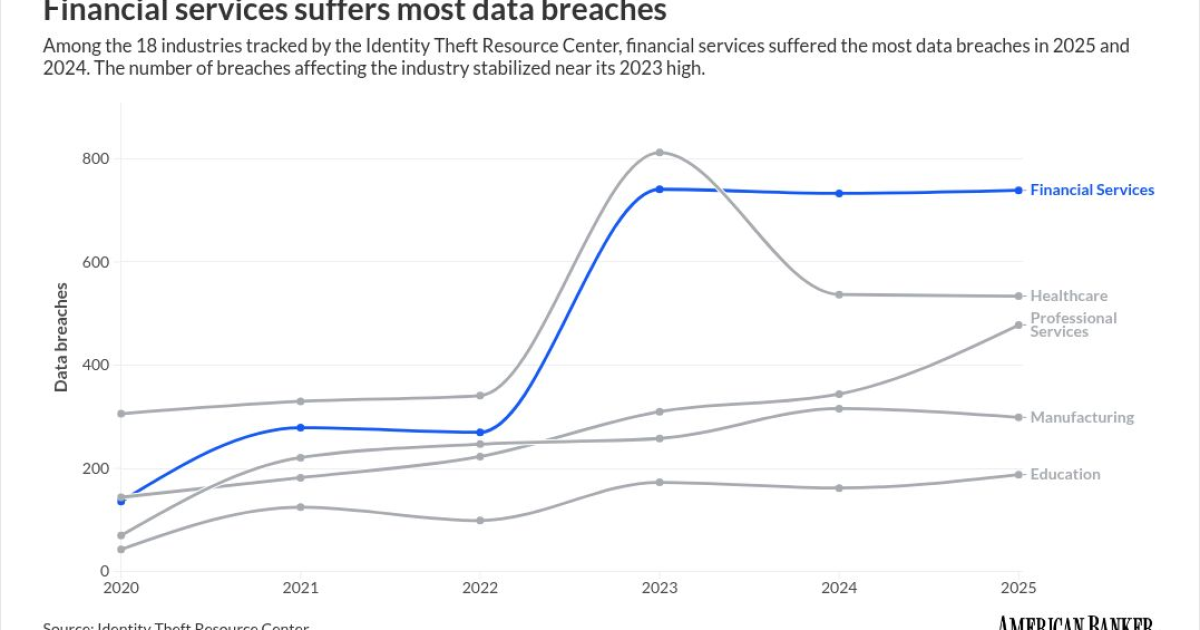
- Supporting data: The financial services sector saw 739 data compromises in 2025, the highest of any industry for the second consecutive year.
- Key insight: "Skimming 2.0" marks a resurgence of physical threats, with criminals deploying Bluetooth-enabled overlay skimmers at points of sale.
- Forward look: Regulators warn that reliance on third parties for critical activities creates concentration risks that require stricter management.
Overview bullets generated by AI with editorial review
The financial services sector suffered the most data breaches of any industry in 2025, topping the list for the second year in a row even as the total number of data compromises in the U.S. hit a record high.
The Identity Theft Resource Center (ITRC) reported 739 compromises in the financial services sector, a slight increase from 733 in 2024, according to its
At the same time, a collapse in transparency has obscured the true nature of the threat landscape to the public; 70% of all breach notices last year failed to disclose the specific attack vector used by criminals, according to the ITRC analysis.
ITRC identified and analyzed 3,322 publicly reported data compromises, which all together yielded approximately 278.8 million victim notices, between Jan. 1, 2025, and Dec. 31, 2025.
The ITRC noted that the data is a conservative estimate because it relies on public reporting; many state laws do not require notification if an organization determines there is "no risk of harm," and many small breaches do not trigger reporting thresholds.
For U.S. bankers, the report signals a shifting risk environment where professional services firms are increasingly utilized as "stepping stones" to access client data, while so-called "skimming 2.0" tactics represent a resurgence of physical threats at the point of sale.
While the volume of compromises in financial services settled near 2023 highs, the sector remains the primary target for bad actors.
Skimming 2.0: A physical threat starts to return
Physical card skimming attacks recorded by ITRC declined to nearly zero in 2024 but increased notably in 2025, something ITRC termed "skimming 2.0."
James E. Lee, president of ITRC, attributed the increase in a statement to American Banker as being "driven almost exclusively by advances in tech."
The number of reported skimming incidents rose from just four in 2024 to 34 in 2025. Criminals are increasingly deploying Bluetooth-enabled overlay skimmers that are difficult for consumers to detect, according to the ITRC report.
While the absolute number of reported incidents in the ITRC data is comparatively low — Lee attributed this to the card industry previously changing its standards to require chip cards and PINs at gas pumps — the financial impact is substantial.
Skimming-related crimes cost businesses and consumers an estimated $1 billion annually, though some industry experts believe the true figure approaches $50 billion due to underreporting, according to
Additionally, the jump in skimming attacks last year "indicates that any organization where debit or credit cards are swiped needs to pay attention to the attack vectors and prepare to defend against these new attacks," Lee said.
Card skimming has regained focus from law enforcement, as well. Operations by the U.S. Secret Service prevented more than $400 million in fraud losses related to card skimming in 2025, according to
Furthermore, FICO data confirms that card skimming compromise events increased in 2023 and 2024, driving counterfeit fraud rates higher for non-prepaid debit card transactions.
Supply chain and professional services risks
Supply chain attacks — data breaches in which the attacker reaches the breached organization by going through one of its tech vendors — doubled between 2021 and 2025. Approximately 30% of all breaches now involve a third party.
Specifically, the ITRC identified the professional services sector — which includes law firms, accountants, and consultants — as the area with the most aggressive growth in compromises. Attacks on these firms increased 39% year-over-year and 162% over a five-year period.
Criminals are increasingly using these vendors as "stepping stones," as ITRC called them, to compromise the networks of their corporate clients, including financial institutions.
"Cyberattacks are now routinely impacting second and third-degree vendors that historically have been beyond the visibility of a prime contractor," Lee told American Banker.
Among tech vendors that power banks' IT supply chains, concentration risk presents a well-known systemic vulnerability.
Just 150 companies power 90% of Fortune 500 technology products, creating chokepoints where one vulnerable supplier can trigger widespread disruption, according to
The Office of the Comptroller of the Currency (OCC) emphasized the importance of concentration risk in its
The transparency crisis
A defining trend of the 2025 report is the decline in actionable intelligence derived from breach notices.
In 2020, nearly 100% of organizations provided details on the root cause of a breach, according to ITRC analysis. By 2025, that figure collapsed to just 30%.
"When organizations withhold the root cause of an attack to mitigate their own legal or reputational risk, they leave the American consumer and other businesses in the dark," Lee said in
For bankers, this lack of transparency complicates risk assessment and third-party due diligence. Without clear data on how vendors are being compromised, institutions face greater difficulty in calibrating their defenses against emerging threats.
One countervailing force is that financial institutions "are among the best prepared organizations and have a solid mechanism for information sharing," Lee told American Banker. Namely, that mechanism is the Financial Services Information Sharing and Analysis Center (FS-ISAC).
"The regulatory structure that applies to financial institutions also tends to foster more transparency and information sharing that does not exist for most non-public and non-regulated companies," Lee said.



